According to a 2024 report from Indusface, malware is a primary threat, with 75 percent of surveyed organizations reporting they were affected by ransomware more than once in the past year. Cyber Essentials, the U.K. government’s five-control playbook, is designed to protect against the majority of common cyber attacks. The NCSC states that implementing these controls can prevent ‘the most common attacks’. In the pages ahead, we map each control to hands-on hardening steps, flag the exact evidence auditors want to see, and keep every tip bite-sized so you can lock down code — and earn the badge — today.
Table of Contents
Cyber Essentials in a nutshell
Cyber Essentials is the U.K. government’s baseline cyber-hygiene standard. You lock down five areas — firewalls, secure configuration, user access control, malware protection, and patch management — and show auditors that the controls stay in place year-round (NCSC, 2024).
The payoff is measurable. In a 2022 Tanium study of UK-based IT decision-makers, 86 percent of those who experienced a breach in the prior six months believed more investment in preventative measures would have minimized the incidents. Cyber Essentials guides teams to the highest-value fixes instead of spreading effort thinly.
Certification comes in two flavors:
- Cyber Essentials: a self-assessment you complete online. Vanta’s Cyber Essentials checklist breaks the process into eight actionable steps, and most applicants finish in two to seven days.
- Cyber Essentials Plus: the same questionnaire plus an independent audit that includes vulnerability scans and spot tests. Both badges expire after 12 months, and you must renew them to stay valid (according to Hut Six).
Quick reference for web applications:
| Control | Web-app focus |
| Firewalls | Close every port except 443; place a web application firewall (WAF) in front |
| Secure configuration | Remove defaults, force HTTPS, add security headers |
| User access control | Enforce MFA, unique logins, least-privilege roles |
| Malware protection | Run AV on servers, scan all uploads, vet third-party scripts |
| Patch management | Apply high-severity fixes within 14 days |
With the essentials clear, we can dive into each control and harden your code step by step.
1. Firewalls – protect the perimeter
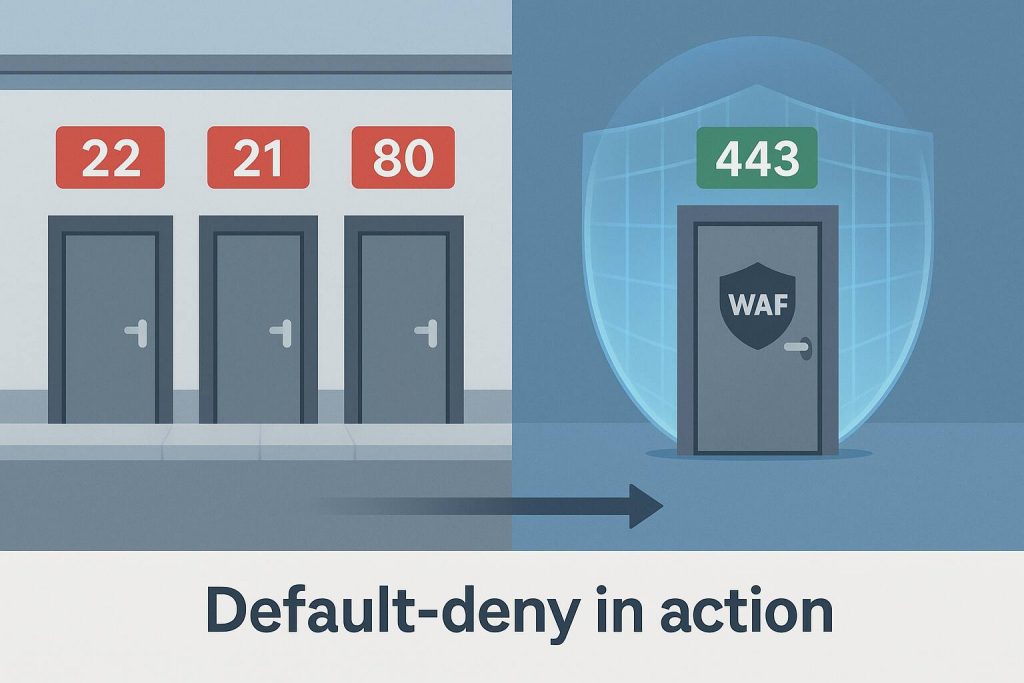
Think of your web server as a storefront on Main Street. The firewall is the glass door that welcomes paying customers on port 443 while shutting everything else out. Close unused ports, and attackers lose most entry points. Attackers frequently scan for and target common service ports. For example, a 2021 report noted a 45 percent increase in attacks against the healthcare sector, including ransomware and DDoS attacks, highlighting the broad nature of external threats.
Start with an external nmap scan. Block or VPN-restrict any service you do not need, such as SSH, old database listeners, or dormant FTP. The National Cyber Security Centre calls this a default-deny stance for inbound traffic.
Place a Web Application Firewall in front of your site. Independent 2023 testing showed that top-tier WAFs detected more than 97 percent of malicious requests and kept false positives under 1 percent, according to OpenAppSec.
Lock down admin interfaces next. Limit your CMS, cloud console, and SSH to known IP addresses, or route them through a single jump host protected by MFA. Replace every default password before the server goes live.
Finally, turn on logging and alerts. A spike in blocked requests or a sudden port sweep is an early warning sign; forwarding firewall logs to your SIEM, or even to email, gives you time to act before a probe becomes a breach.
Cyber Essentials Plus auditors run the same outside-in scans. If your port list is clean and the WAF blocks their test payloads, you pass with minimal fuss, and the internet only sees the doorway you choose.
2. Secure configuration – lock the doors from the inside
Misconfiguration remains the top cloud-breach root cause, linked to 31 percent of incidents in 2024, according to the Thales Cloud Security Study. Cyber Essentials reduces that risk by requiring every default to be reviewed and either hardened or removed.
Strip the extras. Uninstall demo plug-ins, sample apps, and any package the site does not rely on. A forgotten phpinfo() page can expose your whole stack.
Disable weak protocols. If the site serves only HTTPS, block directory browsing and turn off SSL and TLS 1.0. The PCI Security Standards Council banned early TLS after June 30, 2018 because no patch fully repairs its flaws, according to the PCI SSC.
Fail quietly. Replace verbose error screens with a simple 500 message that hides stack traces from visitors but logs full details for developers.
Force encryption end to end. Redirect every HTTP request, set an HSTS header of at least 31,536,000 seconds (12 months is OWASP’s recommendation), and disable weak ciphers.
Add browser-side shields. Send Content-Security-Policy, X-Frame-Options, and X-Content-Type-Options headers so the browser blocks cross-site scripting, click-jacking, and MIME-type sniffing before they reach your code.
Protect secrets. Search for hard-coded passwords, rename or remove default admin accounts, and store credentials in a secrets vault. If a teammate can read prod passwords in plain text, attackers can as well.
Prove it on paper. Keep a one-page checklist of every flag you flipped. Auditors, and future you, can see at a glance why each setting exists and when it was last reviewed.
Tighten these screws now, and you will enter the Cyber Essentials audit with the entire secure-configuration column already green.
3. User access control – prove you are who you say you are
Stolen credentials remain the top entry point. Verizon’s 2024 DBIR reports that the use of stolen credentials was the initial action in 24% of breaches. The remedy is disciplined identity management.
Require strong, unique credentials. Set a minimum of 12-character passphrases, and block anything that appears on known breach lists.
Turn on multi-factor authentication everywhere. Microsoft research found that MFA prevents more than 99.9 percent of automated account-compromise attempts. Cyber Essentials therefore mandates MFA for every cloud admin and user account.
Ban shared logins. Give each person a named account and the least privilege required for the role. Developers deploy code, finance pulls reports, and no one holds super-admin rights by default.
Harden sessions. Issue fresh tokens at each login, mark cookies Secure and HttpOnly, and time-out idle sessions quickly. A stolen token loses value within minutes.
Review and prune quarterly. Run an access audit every three months, disable dormant accounts, rotate elevated credentials, and record the date. Auditors will look for that evidence.
Show Cyber Essentials assessors your MFA dashboard, last access-review report, and role diagram, and this control turns from weak spot to strength.
4. Malware protection – keep bad code off your box
Ransomware still begins with a payload. Sophos’s ‘State of Ransomware 2024’ report found that email-based approaches (including malicious emails and phishing) were the identified root cause in 34% of ransomware attacks., underscoring why email security remains a frontline defense even in broader frameworks like Cyber Essentials. Cyber Essentials counters that risk by requiring real-time malware defense on every system in scope.
Put eyes on the server. Install reputable endpoint protection, enable real-time scanning, and pull new signatures at least once every 24 hours, a hard requirement in the Cyber Essentials questionnaire.
Scan what users upload. Accept only the file types your app truly needs — PNG, PDF, and maybe CSV — and virus-scan each upload the moment it lands. Attackers often rename a script “invoice.pdf,” and the scanner will catch the mismatch.
Police third-party JavaScript. Magecart web-skimming remains a significant threat. Research in 2024 highlighted a 103% increase in Magecart infections over just six months and new attack kits that enabled threat actors to infect hundreds of e-commerce sites. Lock your Content-Security-Policy to trusted domains and add Subresource Integrity (SRI) hashes so a tampered script will not run.
Prepare for the one that gets through. Keep versioned, off-site backups of both data and configs. If ransomware encrypts today’s files, roll back to yesterday’s copy and move on.
Cyber Essentials Plus assessors often upload the harmless EICAR test file. If your controls flag or quarantine it instantly, you pass, and you prove bad code has no future on your servers.
5. Security update management – patch early, patch always
Attackers keep gaining speed: Google Cloud’s threat-intel team measured the average time to exploit at just five days in 2023, down from 32 days in 2021. Yet patching cadence remains a challenge. A 2023 Sonatype survey found that 39 percent of organizations take more than a week to mitigate known open source vulnerabilities after they become aware of them. The practical answer is real-time visibility into new vulnerabilities the moment they surface. A continuous compliance platform such as Vanta pulls National Vulnerability Database updates as soon as they publish and routes high-severity CVE alerts to Slack within minutes; with that signal in place, meeting Cyber Essentials’ fourteen-day patch deadline turns into a routine task instead of a last-minute scramble.
Inventory everything that runs in production. List the OS, web server, framework, database, container base images, and firewall firmware. You cannot patch what you do not track.
Surface new CVEs the same day they land. Wire tools such as Dependabot, OS package auditors, or cloud-native scanners into your pipeline so alerts appear automatically.
Follow the Cyber Essentials rule: high or critical patches within 14 days. This deadline appears in the 2024 CE question set, and auditors will ask for proof. Automate where possible, schedule weekly maintenance windows for the rest, and log each change.
Track platform layers too. Rebuild containers on updated base images, rotate AMIs, and flash appliance firmware. A stale OpenSSL library in a Docker layer is as dangerous as an unpatched host.
Verify with continuous scans. Run weekly vulnerability scans; if a CVE you thought you fixed still shows up, investigate until the report is clean. A spotless scan before your CE Plus audit is the closest thing to a guarantee.
Patch discipline feels routine, but it removes entire exploit classes overnight and costs far less than any new product.
Continuous compliance – stay audit-ready every day

A Cyber Essentials badge captures a moment in time, while threat actors work around the clock. One Titania study found that misconfigurations cost organizations an average of 9 percent of annual revenue, largely because most devices are audited only once a year. Continuous monitoring closes that gap.
Automate the watch. Platforms such as Vanta, AWS Security Hub, or even a Bash script can poll for open ports, missing patches, or new user accounts, then flag drift in Slack within minutes. IBM’s 2023 Cost of a Data Breach Report shows that organizations with extensive use of security AI and automation experienced $1.76 million lower data breach costs and identified and contained breaches 108 days faster than those with no use.
Let automation gather evidence. Screenshots, patch logs, and MFA metrics accumulate silently in a secure vault, so next year’s auditor receives a timestamped trail without a last-minute scramble.
Run a fire drill every quarter. Perform an external scan, review firewall rules, and disable dormant accounts. Small, frequent fixes beat crisis weekends.
Track the rulebook. The National Cyber Security Centre updates Cyber Essentials questions each year. The 2025 “Willow” set arrives in April; subscribe to their bulletins so new mandates, such as universal MFA or shorter patch windows, enter your backlog rather than your blind spot.
Continuous compliance spreads the workload over 12 months and turns the next audit into a victory lap instead of a cliff-edge rush.


















Leave a Reply